Port Scanning Timeline
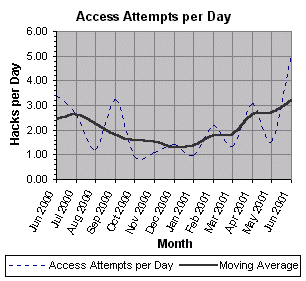
For more information on what happened in each month, see my monthly report.
Access Attempts by ISP
I have found that I have experienced access attempts from the customers of too many ISPs to realistically show that information in a pie chart. The pie chart is still available if you are interested however – just click here. The majority of access attempts (64%) appear to be from BT Internet customers. You may think that BT Internet is rather friendly to hackers with statistics like that (they’re not that bad 🙂 ). The reason for this is that BT Internet is my own ISP – hackers tend to target other customers of their own ISP more (hackers can’t be bothered to go out and find out the IP addresses for any other ISPs!).
Access Attempts by ISP
I have found that I have experienced access attempts from the customers of too many ISPs to realistically show that information in a pie chart. The pie chart is still available if you are interested however – just click here. The majority of access attempts (64%) appear to be from BT Internet customers. You may think that BT Internet is rather friendly to hackers with statistics like that (they’re not that bad 🙂 ). The reason for this is that BT Internet is my own ISP – hackers tend to target other customers of their own ISP more (hackers can’t be bothered to go out and find out the IP addresses for any other ISPs!).
Mirror Sites
Should I ever leave BT Internet for some reason, this website would disappear. Because of this, I have created a mirror site with Connect Free. Hence, you can access my web pages from any of these 2 addressees:
http://www.shawweb.connectfree.co.uk/george/hacks/http://www.shawweb.btinternet.co.uk/george/hacks/
So, if you can’t access my website, you know where to go!
Should I ever leave BT Internet for some reason, this website would disappear. Because of this, I have created a mirror site with Connect Free. Hence, you can access my web pages from any of these 2 addressees:
http://www.shawweb.connectfree.co.uk/george/hacks/http://www.shawweb.btinternet.co.uk/george/hacks/
So, if you can’t access my website, you know where to go!
Protect Yourself!
To be fully protected from hackers, you need a firewall of some kind. My favourite is ZoneAlarm. See About Firewalls for more information. A good, up-to-date anti-virus program wouldn’t go a miss either.
To be fully protected from hackers, you need a firewall of some kind. My favourite is ZoneAlarm. See About Firewalls for more information. A good, up-to-date anti-virus program wouldn’t go a miss either.
Beware of Terminology
There is a fine line between port scanning and hacking. Port scanning is simply checking to see if a computer will respond to access attempts on a certain port. This activity is quite legitimate on its own – it can be used to test the performance of a network, or to test for the presence of unwanted server software. However, it is quite commonly used for more malicious purposes, such as testing for the presence of a backdoor program for the purpose of using such a program to perform damage.
Once a port on a computer has been scanned, and has been determined to be responsive to access attempts, a hacker could then proceed to do the actual hacking – ie gaining unauthorised access to data. On this website I do tend to use “hacking” as an umbrella term to cover any kind of unauthorised access attempts. I have no proof that the intent behind any port scan is malicious, but it seems likely given that the ports used by these scans are in common use by backdoor programs such as SubSeven.
Also note that some forms of backdoor and virus software can cause a person’s computer to port scan and hack into other computers without the knowledge of that person. See my FAQ page for more information.
Another bit of common confusion is the difference between a hacker and a cracker. A hacker is an enthusiastic programmer, whereas a cracker is someone who attempts to gain unauthorised access to data. I probably don’t help relieve this confusion very much, since I myself refer to ‘hackers’ where I mean ‘crackers’. This is because I feel that most people are probably more familiar with the word ‘hackers’, no matter how technically incorrect it is. Again, see my FAQ page for more information.
There is a fine line between port scanning and hacking. Port scanning is simply checking to see if a computer will respond to access attempts on a certain port. This activity is quite legitimate on its own – it can be used to test the performance of a network, or to test for the presence of unwanted server software. However, it is quite commonly used for more malicious purposes, such as testing for the presence of a backdoor program for the purpose of using such a program to perform damage.
Once a port on a computer has been scanned, and has been determined to be responsive to access attempts, a hacker could then proceed to do the actual hacking – ie gaining unauthorised access to data. On this website I do tend to use “hacking” as an umbrella term to cover any kind of unauthorised access attempts. I have no proof that the intent behind any port scan is malicious, but it seems likely given that the ports used by these scans are in common use by backdoor programs such as SubSeven.
Also note that some forms of backdoor and virus software can cause a person’s computer to port scan and hack into other computers without the knowledge of that person. See my FAQ page for more information.
Another bit of common confusion is the difference between a hacker and a cracker. A hacker is an enthusiastic programmer, whereas a cracker is someone who attempts to gain unauthorised access to data. I probably don’t help relieve this confusion very much, since I myself refer to ‘hackers’ where I mean ‘crackers’. This is because I feel that most people are probably more familiar with the word ‘hackers’, no matter how technically incorrect it is. Again, see my FAQ page for more information.

Leave a Reply